Why Choose Encrypted File Transfer For Better Solution?
Sometimes,
the internet becomes a scary place for businesses, which is clearly
why many are paying closer mind to best practices in order to secure
up the transfer of the file. Encryption is one of the finest
practices for data securing.
Three
Key options for Encrypted
File Transfer
-
FTPS (File Transfer Protocol Secure),
-
HTTPS (HTTP Secure),
-
SFTP (SSH File Transfer Protocol)
These
three options are widely used for external to internal and business
to a business transfer. Let discuss the basics at first.
What
is Encrypted File Transfer?
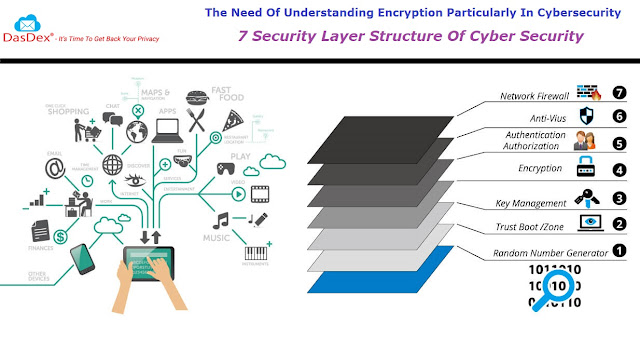
Known
as an important security measure, file transfer encryption is widely
used to prevent outsiders from being capable to read or recognize the
data that is being transferred. It directly defends the information
from high possibilities hackers. In case, the data is encrypted, the
details get controlled into an unidentifiable set-up during the
transit, and after reaching the final destination, the data turns
readable once again. In the way, the data is just accessible by those
it is planned for.
Uninterrupted
Encryption Options
The
quickest of the three file transfer encryption choices and the most
commonly executed is FTPS. It includes explicit and implicit notes,
but they equally use SSL encryption. With FTPS understood SSL, the
server and client institute an SSL session prior to any data can be
wired. Moderately, in FTPS open SSL, the client and server decide
mutually what level of encryption ordinary is necessary for the
transfer of data. It is supportive as the encrypted FTPS and
un-encrypted FTP can happen at an individual port. However, this
can't always happen and wide range of data ports should be offered
for usage.
However,
SFTP and FTPS are wonderful to use within servers. The HTTPS is good
for human-based and interactive transfers. It is easy to find HTTPs
at work even in the web portal we use for Large
File Transfer.
HTTPS defends data derived between the website and web browsers.
The
web browsers such as Firefox and Chrome even visually show this
security with the help of locked padlock in the bar of the security.
HTTPS makes use of the SSL or TSL protocols. Similar to SFTP, HTTPS
even makes use of the Public Key Infrastructure. In the system, the
private, as well as public keys, focus on each other. Data encrypted
and websites with the public key can just be decrypted with the
assistance of private key and vice-versa.
Switzerland
Office
Codebase
AG
Haldenstrasse
5 CH-6006, Luzern, Switzerland.
+41
41 312 13 91
India
Office
Codebase
Technologies Private Limited
427
First floor, Udyog Vihar Phase 3, Gurgaon, Haryana, India
+91
124 4203552


Comments
Post a Comment